Security Term
Introduction/Purpose:
The Security Term Master encompasses a diverse set of security considerations, including elements such as bank guarantee, letter of credit, intellectual property protection, physical security, cybersecurity, and compliance with laws and regulations. It is designed to facilitate collaboration between two or more entities, such as individuals, firms, or companies. Serving as a comprehensive reference guide, it ensures that the procuring organization and suppliers have a shared understanding of the security requirements and expectations.
Dependency:
The creation of the Security Term Master in a procurement system depends on several factors. Here are some key dependencies involved:
- Vendor: Before recording security terms, the procurement team identifies and selects vendors who are eligible to participate in the procurement process. This may involve a vendor evaluation and selection process based on factors such as capabilities, experience, financial stability, and compliance with procurement policies.
These dependent fields help structure and organize the Security Term Master within the procurement system, enabling efficient management, retrieval, and implementation of the security terms and requirements throughout the procurement process.
How to Navigate:
The navigation to record a security term in a procurement system typically involves the following steps:
- Click on the main navigation icon: The main navigation icon may be located in the top right corner of the screen. Clicking on this icon will open the navigation menu, which typically includes links to various sections of the procurement system.
- Click on the Other Master section: The Other Master section is located under the left section of the screen; clicking on this section will display a list of masters related to procuring.
- Find the Account/Finance section: The Vendor section is located in the list of Masters under the Master section. Clicking on this section will display a list of masters related to the account/finance.
- Click on the Security Term link: The Security Term link is located under the Account/Finance section; after clicking on this link, you can navigate to Security Term in the listing, and from that you can easily upload new transactions into the system.
Listing:
A security term listing provides a concise overview of the security terms associated with vendors in a procurement system. It typically includes the following information in a card format:
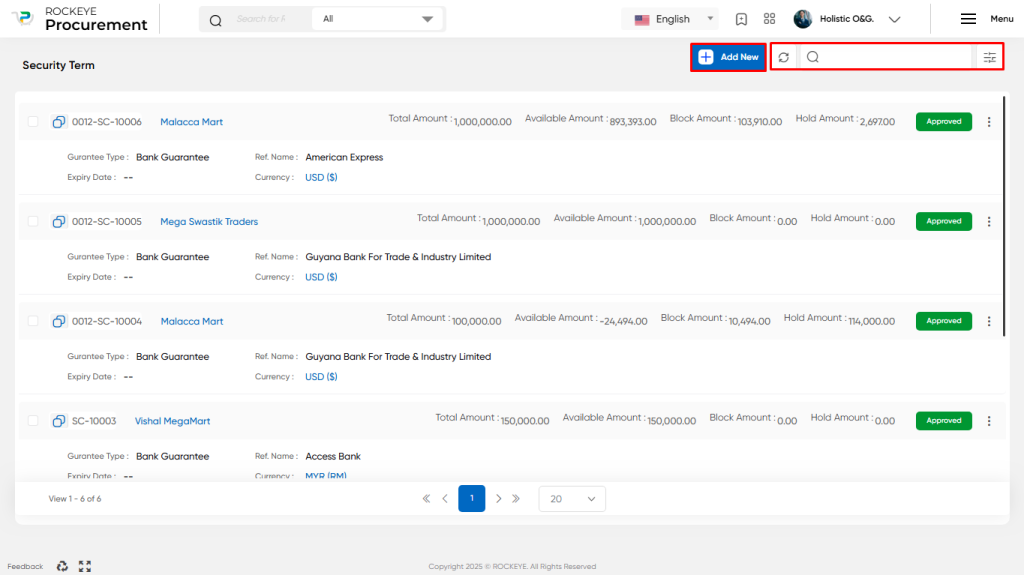
- Basic Search, Export, Refresh, Filter: The listing provides a user-friendly search function to quickly find security term masters based on their names, codes, or other relevant criteria. The refresh option ensures that the listing is up-to-date, and the filter function allows users to refine their search based on specific attributes.
- Card View: The listing presents the Security Term Record in a card view format, where each vendor is displayed as a card containing important details. This includes the vendor’s name, Security Term code, Type of Guarantee Document, Currency, Expiry Date, Total Amount, Available Amount, Block Amount, Hold Amount, approval status, Other details can found, like Activity Log, Blocked Payments, and All Transactions, in the More Options menu. The card view provides a concise and visual representation of key security term information, facilitating quick and easy reference.
The security term listing provides a convenient way to search, filter, and refresh the displayed information, allowing users to quickly access and review the relevant details of the security terms associated with vendors in the procurement system.
Recording & Update:
Recording and updating transactions in a procurement system involves capturing and maintaining relevant information regarding security terms. The following fields are typically included in the process:
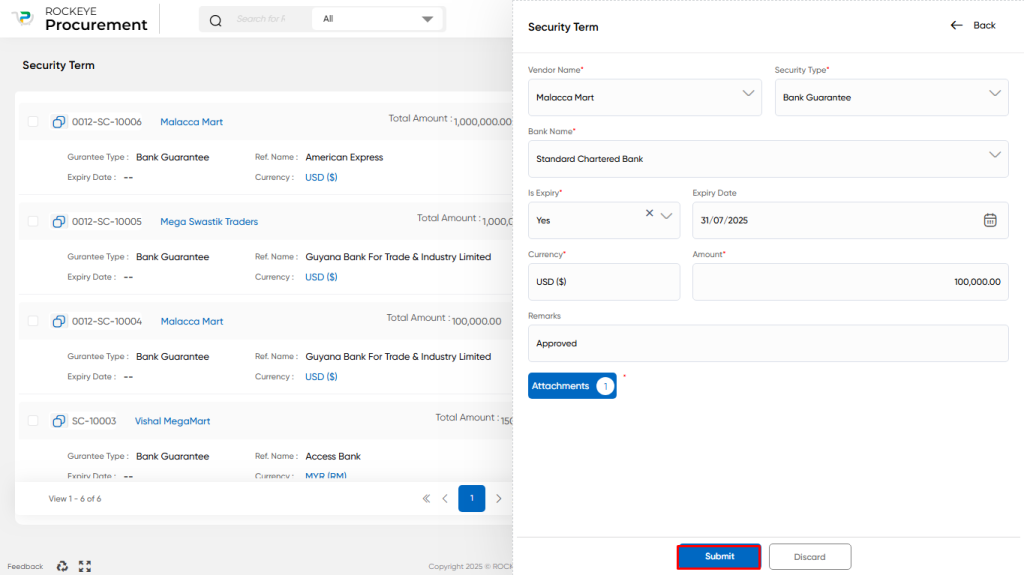
- Vendor: This field is used to select the vendor associated with the security terms.
- Security Term: This field allows for the selection of the type of security being used. It may include options such as bank security, letter of credit, or other types of security.
- Bank Name/Ref Document: If bank security is chosen, this field captures the name of the bank. If a letter of credit is selected, the field captures the reference document associated with it. For other types of security, the field may capture the contact person’s name and contact number.
- Expiry: This field indicates whether the security has an expiry date or not.
- Expiry Date: If the document has an expiry date, this field captures the specific date on which it expires.
- Currency: This field captures the currency in which the security amount is denominated.
- Amount: The amount field represents the value of the security.
- Remark: This field allows for any additional comments or remarks regarding the security terms.
- Attachment: This field is mandatory and requires the attachment of a relevant document, such as the security agreement or letter of credit.
By accurately recording and updating these fields within the procurement system, the organization can maintain a comprehensive and up-to-date record of the security terms associated with each vendor and transaction. This helps ensure proper compliance, risk management, and smooth procurement processes.
The user can perform the following actions in this section:
- Submit: This option allows the user to publish the transaction information. If the system has an approval flow, the maker will submit the information, and it will be sent to the approval authority or checker for approval.
- Discard: This option allows the user to discard the transaction before saving it.
Key Notes Security Term:
- Once security terms have been set for any vendor, they can be viewed in the vendor master section of the business information as “Security.”